Ransomware Impact Analysis
Attackers are sidestepping traditional defenses. A new approach is needed.
Ransomware costs organizations more than $70 billion per year
With an attack occurring every 15 to 20 seconds.
3 out of 4 victims had up-to-date endpoint protection when they were infected.
Passpoint's Ransomware Impact Analysis (RIA) offers a secure means to simulate a ransomware infection within your organization's network. By installing a lightweight agent on 'Patient Zero' and employing the same Tools, Techniques, and Procedures (TTPs) utilized by real attackers, our RIA meticulously traverses the environment. Tracking the specific TTPs used provides invaluable insights to fortify your defenses against actual attacks. RIA conducts a comprehensive analysis, identifying factors that can minimize the likelihood of a ransomware attack and suggesting strategies to mitigate damage if such an event occurs, ensuring your organization is well-prepared and resilient.
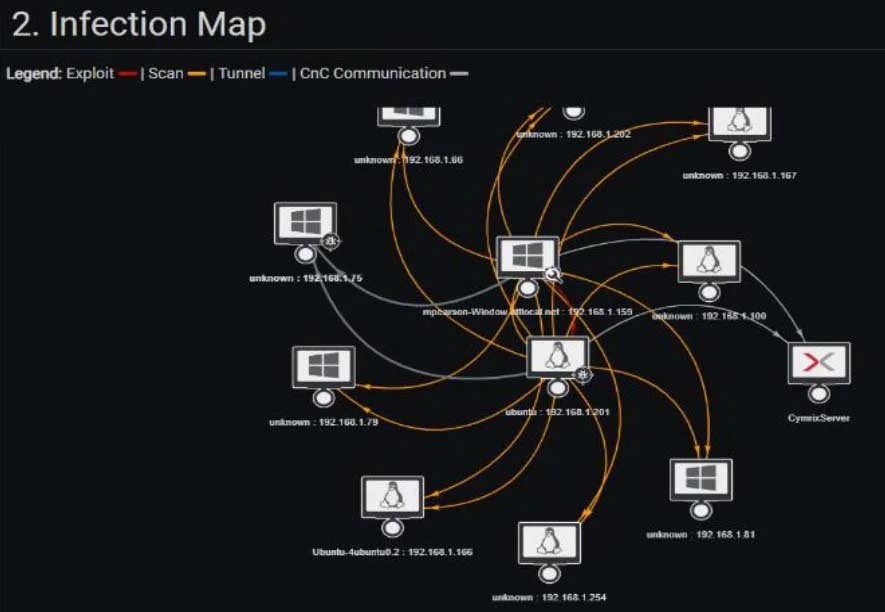
What’s Your Blast Radius?
Based on the attack path, our RIA gives you a detailed list of vulnerabilities and gaps that allows your team to focus resources and budget to close verified gaps.
With its interactive reporting feature, our RIA provides your organization with a visual roadmap to remediate data separation, network segmentation, and user permissions, strengthening your security posture and hardening your environment against infection.
The RIA includes:
Interviews with key personnel and management to understand your organization’s critical data and systems
Review preventive security controls that can reduce the likelihood of ransomware, such as strong authentication
mechanisms and phishing training and awareness
Run multiple live-fire ransomware simulations of defined network segments
Provide a report with actionable recommendations to help your team reduce ransomware risk and strengthen your
overall security posture.
Provide policy and strategy recommendations to limit the business impact if you do experience a ransomware attack
Reduce your organization’s ransomware attack surface
Recognize operational deficiencies in the management of ransomware-related risks